Privileged Access Management (PAM) for Enhanced Security
Posted February 16, 2022 by Joe Schnell

A big part of protecting your organization from cyberattacks starts with two questions: Who really needs access to critical systems and functions, and how will you grant those individuals access?
Answering those questions is where privileged access management (PAM) comes in. PAM secures and monitors account credentials that have elevated permissions to critical systems including firewalls, servers, and identity sources such as Active Directory. Those credentials have become targets of bad actors who want to break into your environment. In fact:
More than a third of all breaches involve the use of stolen credentials, according to the 2021 Data Breach Investigations Report. Nearly half of the organizations have at least some users with more access than they need for their jobs, says the 2020 Identity and Access Management Report by Cybersecurity Insiders.
If those stats don’t worry you, consider how those credentials are the initial access into your organization. Once an attacker gets into your environment, they can escalate their attack by elevating their permissions, moving around and getting to more critical systems, taking control, and causing more havoc.
The Identity Space: Where PAM Fits
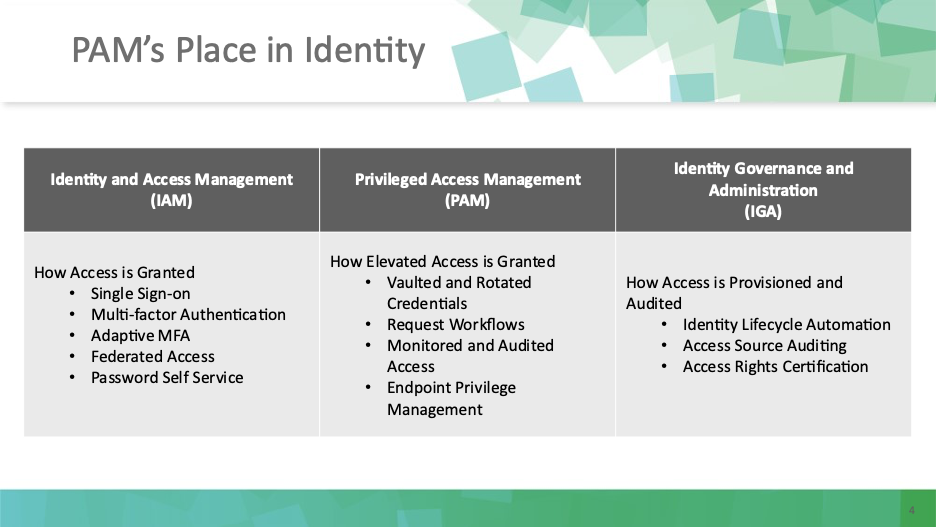
Having the right identity strategies in place improves your cybersecurity resilience, helping you to manage and minimize the human risk inherent in your organization. Think of privileged access management as one of the three legs of the identity management triumvirate:
- Identity and Access Management – How you grant access to systems, such as by using multi-factor authentication.
- Privileged Access Management – How you grant elevated access for high-tier systems, such as by rotating credentials.
- Identity Governance and Administration – How you provision and audit access to ensure people have access to only what they need for their respective roles.
Three Components of Privileged Access Management Solutions
You can choose from a variety of available PAM solutions from various vendors to help ensure your high-risk systems stay secure. When selecting a PAM tool, consider these three key components of the offering:
- The vault – This is the hardened storage location where you put sensitive credentials including your domain admins, local admins, service accounts, database admins, application accounts, cloud management accounts, and SSH keys. By locking these away in the software vault, you can then put workflows in place such as multi-level approval requirements to be able to access them.
- Password management – Specific policies define password length, complexity, and how often to rotate passwords. This is especially important against attacks such as Kerberoasting, which targets and steals Active Directory service account credentials from memory, then attempts to crack them offline and use them to encroach further into your environment.
The password management in a PAM solution protects against attack by vaulting those credentials, using long passwords of 20 or more characters, and regularly rotating them. By the time the attacker has managed to crack the password offline, the system has already rotated to a new password.
- Session management – This area of PAM security focuses on individual sessions by users and includes secure connections as well as session recordings and analysis. Recordings provide videos of the GUI and what the user is doing as they move through the environment, including full keystroke recordings of commands the user typed. You can later review the recordings to determine if users did anything malicious, or monitor recordings in real-time and shut down suspicious activity within privileged accounts.
Benefits of Privileged Access Management
With a PAM software solution, you can have workflows in place with approval processes that reduce the risks of what someone can do with their privileged credentials. Preventing individuals from moving further into your environment protects not only against stolen credentials but also against current or former employees or contractors with privileged access who might want to take retaliatory actions against the company.

PAM tools also reduce the operational overhead for password management by automating the process of rotating credentials regularly.
PAM’s centralized management and auditing of privileged activity provide valuable visibility to suspicious actions. You can see what’s taking place in an individual’s privileged account and quickly respond to it.
For more on this topic, watch the 15-minute “Privileged Access Management, Now More Than Ever” presentation by Joe Schnell from the Sayers #Curio Virtual Tech Summit, now available free on-demand.
Questions? Contact us at Sayers today. We can help you choose the right identity strategies and solutions to protect your organization.
Joe Schnell, Senior Cybersecurity Architect at Sayers
Joe Schnell has extensive experience supporting Sayers clients through architecture, design, product evaluations, and implementation of cybersecurity technologies. He has worked for numerous large enterprises, helping clients align security goals with business needs. Schnell has deep expertise in application and data security, identity, endpoint and mobile security, vulnerability management, and compliance.
Additional resources:
Cybersecurity: Your Human Risk Is Greater Than You Think
Protect Your Organization from Ransomware With Immutable Storage


